Stored XSS into anchor href attribute with double quotes HTML-encoded
This writeup delves into the 8th XSS lab in port swigger.
Stored XSS into anchor href attribute with double quotes HTML-encoded
Introduction
This is a lab for a stored XSS vulnerability. Let’s see what we can do with it.
Investigation
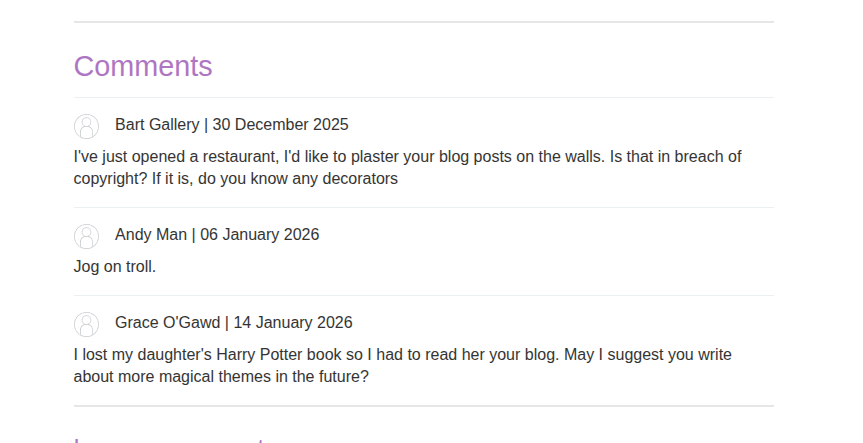
We have almost the same website as usual: a blog with posts. Let’s check a post and try to comment on it.
Our goal is to click the username of a comment and trigger an alert.
The username is rendered like this:
1
<a id="author" href="https://koussaydhifi.org">Injected</a>
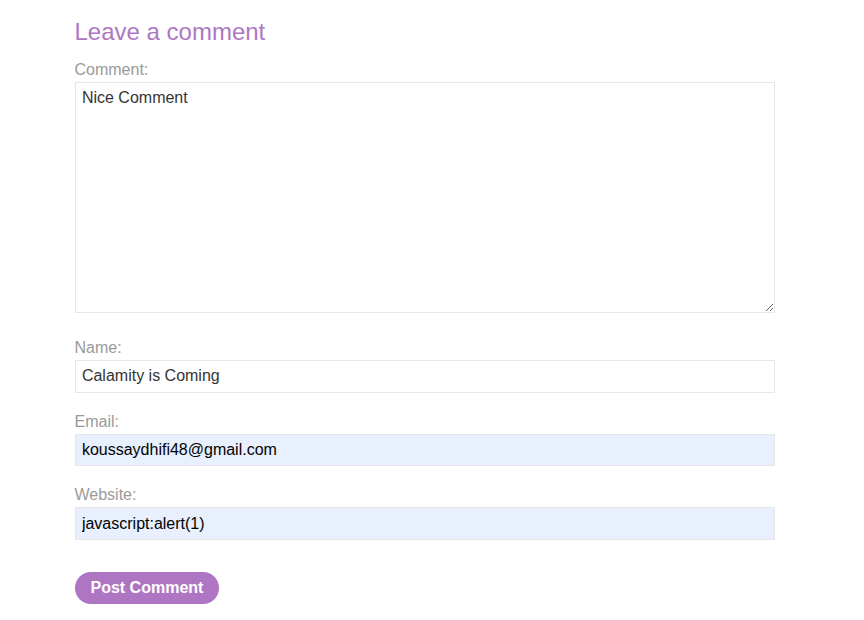
Basically, the href attribute is the key here. So what if we inject a JavaScript URL scheme like javascript:alert(1)?
The href normally points to a website, but in the website input we can add this payload. Then, when you click the username.
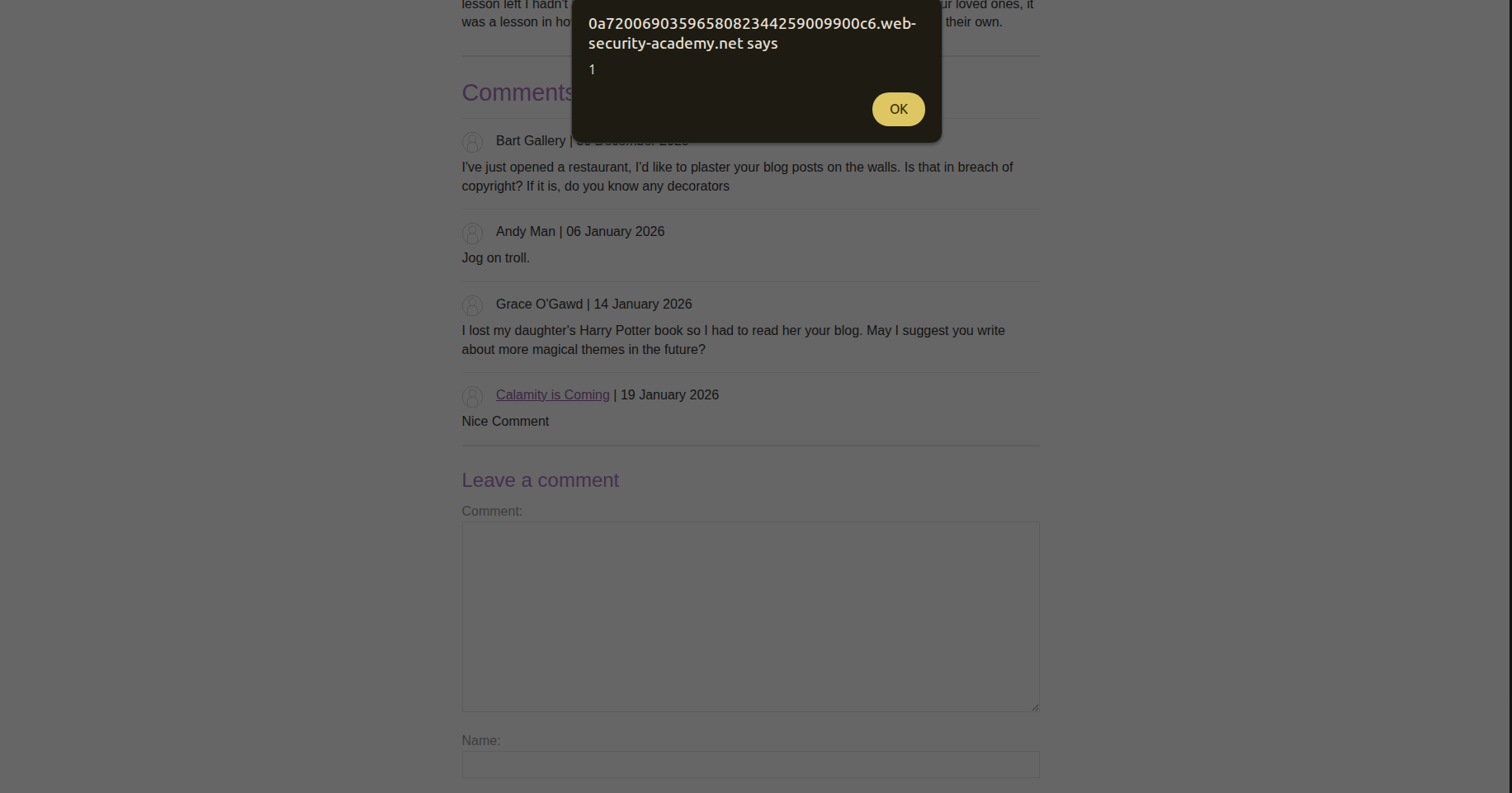
tada — the alert is triggered.
Conclusion
Nice lab. Waiting for the next one, inshallah.
This post is licensed under CC BY 4.0 by the author.